The MacroHard WeakEdge challenge is worth another 60 Points.
It is located inside of the Forensics Category of picoCTF. The Author stated, that he has hidden a flag inside of the given .pptm file. pptm is a PowerPoint format with macros enabled. So, lets start digging into this file!
When opening the file we are greeted by a warning about the possible risks of the contained Macros. Luckily, they are disabled by default.
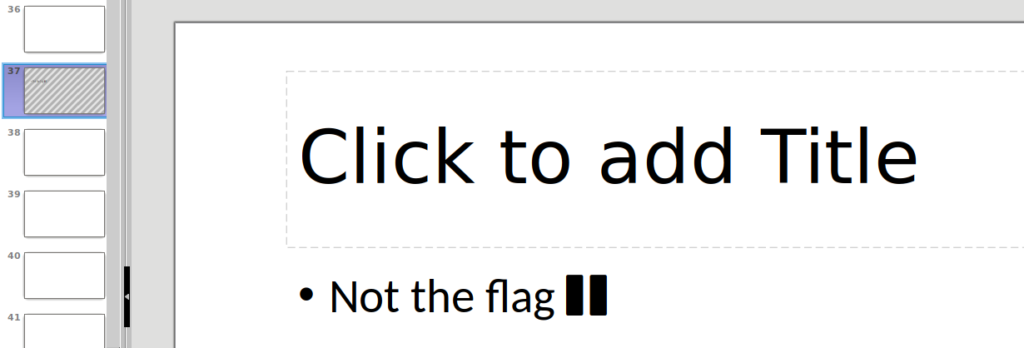
The Power-Point itself is nearly empty. Only on Page 37 we get the info, that this page does not contain the flag we’re looking for.
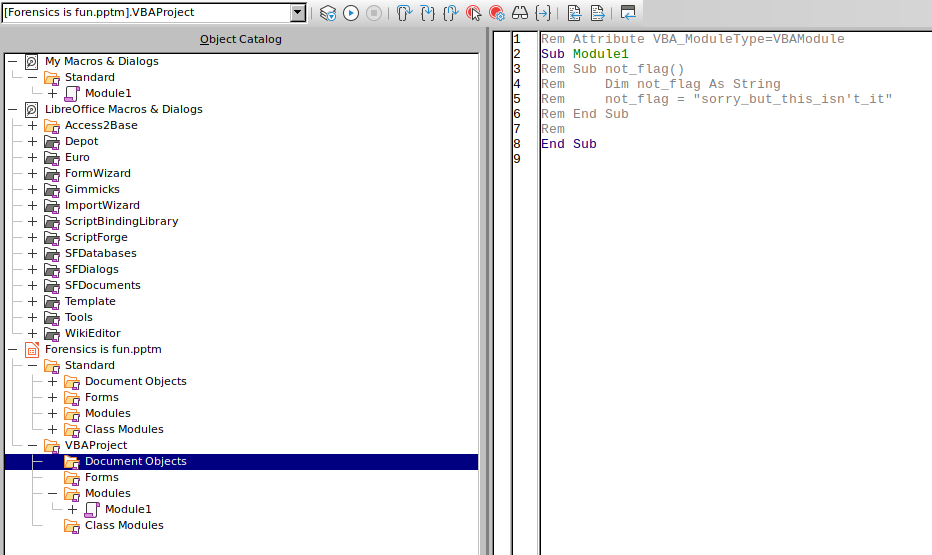
The next step was looking at the macrosection of the file (as this is clearly the hint in the name of the challenge). The VBA (Visual Basic for Applications) / Macro Section does not contain the flag either. So let’s move on.
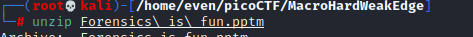
As the flag was not contained in either the plain presentation, nor the macro-side of the file i started to look for hints and different ways to analyze pptm files on the web. I discovered the hint, that pptm files are basically archives that can be unzipped. With using the unzip [filename] command i unpacked the contents of the pptx-file.
After opening some random files i discovered, that the folder slideMasters contained a small file named ‘hidden’. There must be something special about this file as it didn’t seem to fit inside the ppt-contents! The file itself only contains different characters without any further explanation or anything else.
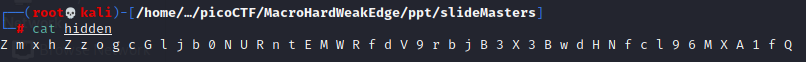
As this didn’t match our expected flag-pattern i thought, when looking at the used characters, that this could be a base64 encoding to hide the flag from search-algorithms. When removing the whitespaces and decoding the flag via shell command i retrieved the flag. Note: The command returned invalid input as the flag did miss the padding at the end (the ‘=’ character is used to fill up gaps if there are not enough bits to do a normal base64 transformation )
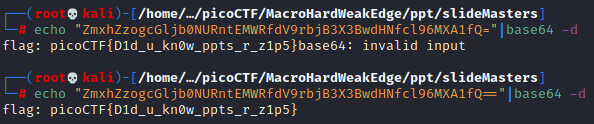
You can use cyberchef to do the decoding-stuff if you are unsure about the syntax when using the shell. I would have done the same if it wasn’t for base64 and me currently working on a page about this…
Challenge solved. 🙂

No responses yet