The ‘Wireshark doo dooo do doo…’- Challenge is worth another 50-Points and honestly – you need to dig deep if you know little to nothing about wireshark as i did. Fortunately there are plenty of informations about this tool out there.
The challenge itself comes without any hints so we have to go blind into this challenge. Of course, the title of this challenge is a hint itself, but lets see.
Wireshark is a software that is used to analyze the network traffic on a microscopic level. It allows us to look at the protocolls and data packages interchanged at the network layer. For this purpose wireshark is somewhat the standard. If you want to take a look at that program you can do that at https://www.wireshark.org/
Wireshark is pre-installed on dedicated Linux-Distributions like kali. if you use another distribution you can install wireshark by using ‘sudo apt install wireshark’. By default, it requires root to run. (If you want to change that requirement: There are a lot of instructions out there. Maybe i’ll do my own tutorial on this at some point.)
But lets move on with this challenge. With using
‘wget https://mercury.picoctf.net/static/ea41c400c[…]d362ab/shark1.pcapng’
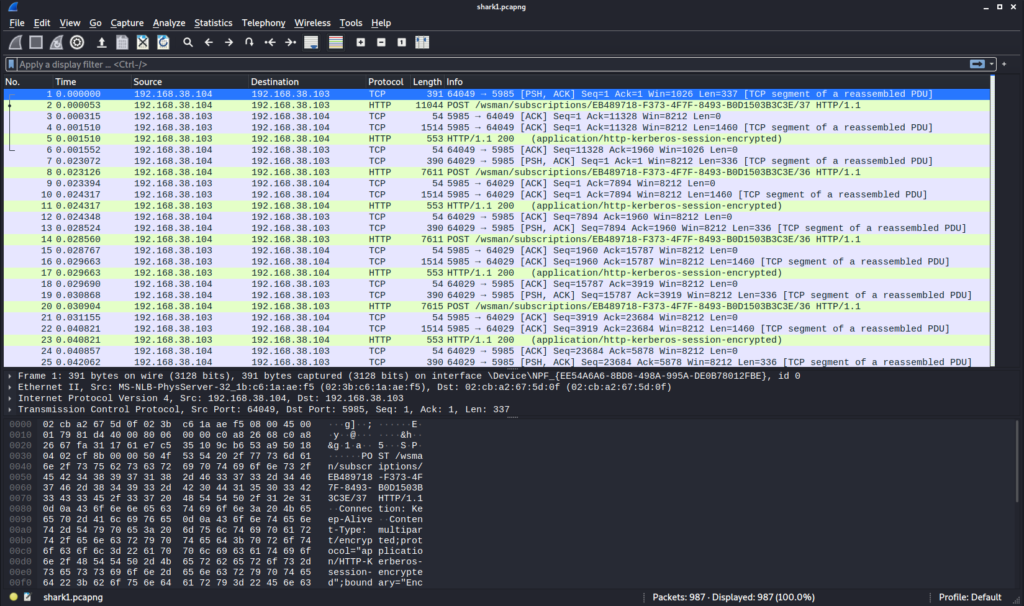
we download a shark1.pcapng file. A .pcapng-file is a dump-protocoll / a dump-file used by the wireshark program. To open the file we need wireshark installed. Then, we can use
wireshark ./shark1.pcapng
to open the file.
Before us lays a ton of network traffic and somewhere in that white noise, there is our flag. Unfortunately, my sledgehammer-method failed right at the beginning. I was trying to simply search for the strings ‘pico’, ‘ctf’ , ‘flag’ etc. at the packet list / detail / bytes-level but i did not find anything. Unlucky me. If the string is not in there, the file either contains an encrypted flag or just a simply pointer to the flag that is stored somewhere else.
As i was not willing to click every single package of the given dump i decided to restrict the displayed packages to HTTP-Packages only. I thought, that the flag couldn’t hide inside the TCP-Protocoll packages like the [ACK] / [PSH/ACK] or ARP ones and the HTTP-ones were the ones looking most promising.
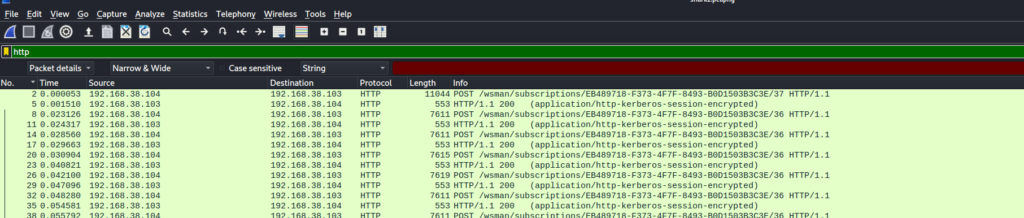
After applying the Filter we see, that every package is encrypted. After scrolling a while, we finally get to a packet that isn’t. Package number 827 consists of text/html. Hey, thats a breadcrumb!
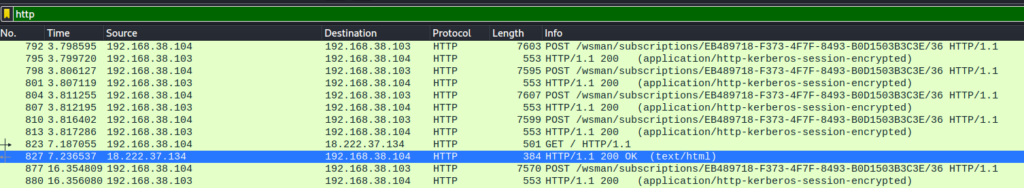
Opening the package in a new window we get 1 line of text/html that looks really promising
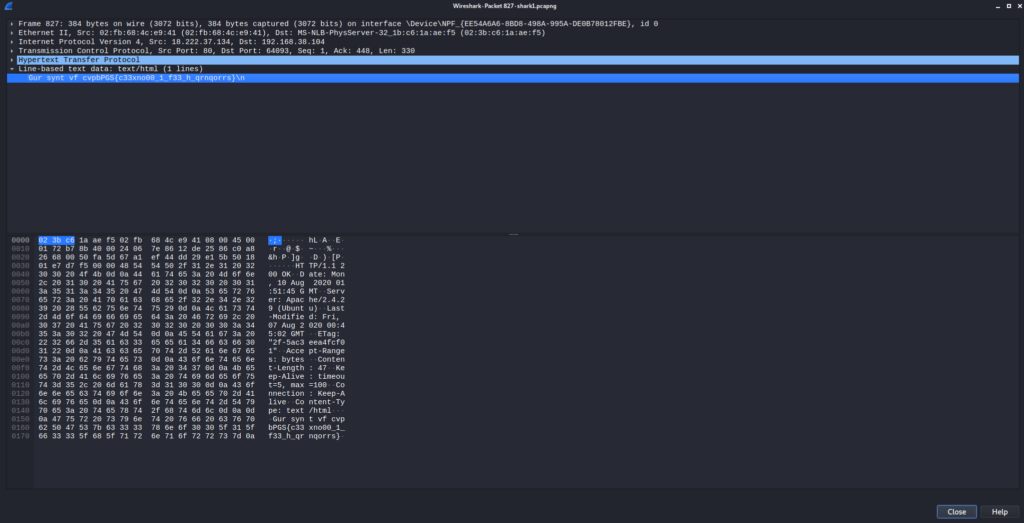
> Gur synt vf cvpbPGS{c33xno00_1_f33_h_qrnqorrs}
This could be the flag we are looking for. The syntax , espacially of the last block of characters, is a clear indicator (curly braces, 4 small characters (pico), 3 big ones (CTF) before them). As this looks really similar to the regular syntax i thought, that it could be encrypted with a simple ROT-Cipher. To try those we can use good old Cyberchef.
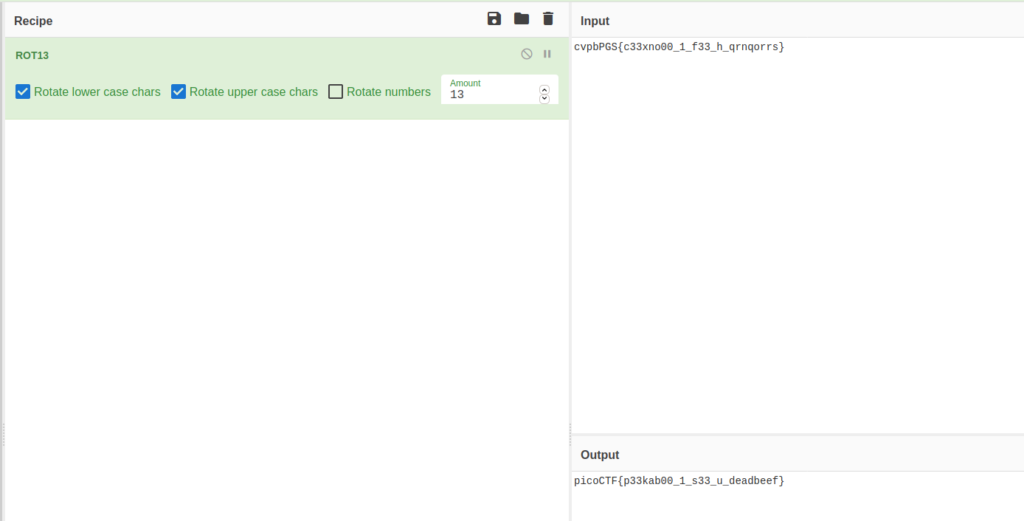
Voilá, thats a bingo! The flag is encrypted with a common ROT13-Cipher.
Submit the flag and move on to the next challenge.

No responses yet